Last week we discussed the basics of two-factor authentication (2FA) and video sex manoharawhy it's a good idea to take advantage of it. If you haven't read the article, I recommend you do, after which you'll likely get used to the idea of having 2FA on some of your accounts.
Just yesterday I had to go into Google Authenticator for a code and when I logged into my GitHub account from my husband's laptop, I needed to enter the code I got by text. But there is another way, and it's a tiny FIDO U2F security key that I've now put on my keychain.
The FIDO U2F Key is less than $20 on Amazon. The key came in a tiny envelope that at first I didn't even see in the Amazon box (it can't be more than 2 x 2 inches.) The key is ready as soon as you unbox it, but if you want to test it out you can use Yubico's website.
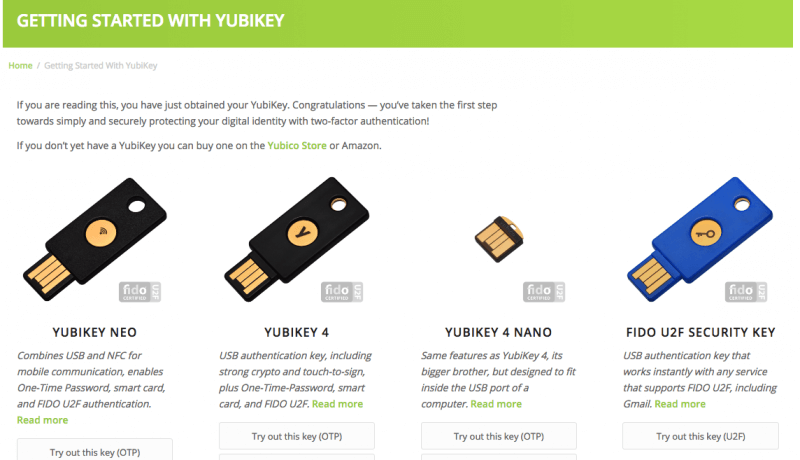
The key I bought is the one on the far right. Next I plugged the key into my PC, it blinked a few times. I entered password/username and clicked next. Registration, done.
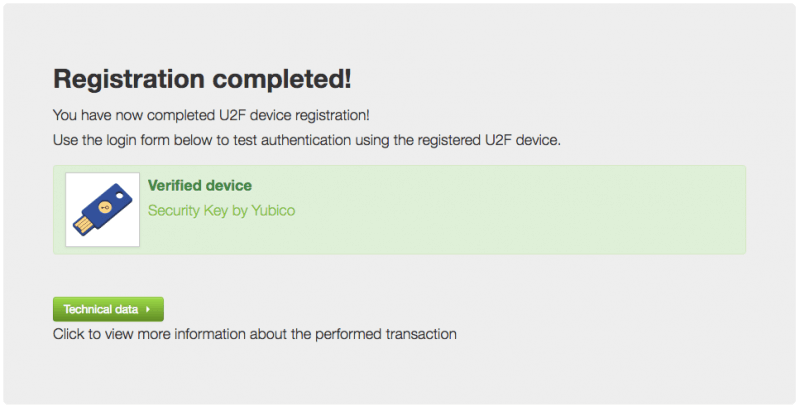
Then I had to log out, log in on a different page and then touch the button/touchpad on the security key to complete authentication.
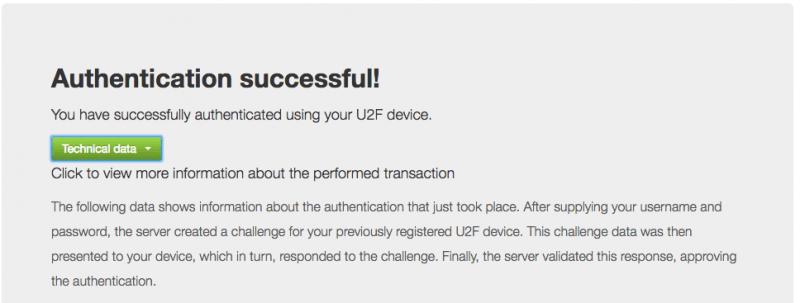
Here's a little more about the FIDO U2F standard:
U2F was created by Google and Yubico, with contribution from NXP, and is today hosted by the open-authentication industry consortium FIDO Alliance. U2F security keys are supported by Google Chrome since version 38 and Opera since version 40. U2F security keys can be used as an additional method of two-step verification for Google accounts, Dropbox, GitHub, GitLab, Bitbucket, Dashlane, Lastpass and the UK's Government Digital Service.
Set up Two-Step Verification for your Dropbox account, if you haven't already. This is also where you will set up your mobile device as a backup in cases where you can't use the key.
Here are the requirements to secure your Dropbox account with the Yubico key:
Once at Dropbox, navigate to your account settings and then Security. Click Security Keys, and then click Add. Enter your password, and click Next. Click Begin setup.
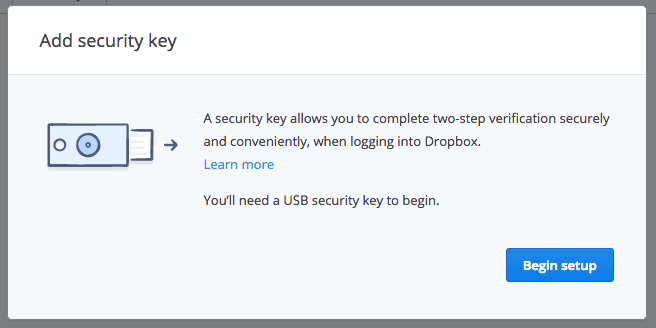
Insert the key, wait a few seconds, and then click Key Inserted. When you see the message "Scanning for security key," your key should start to flash. Wait for it to blink, and tap the button.
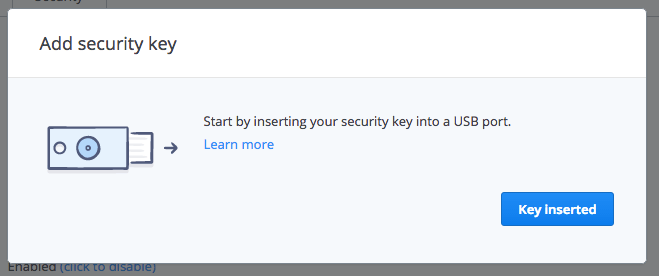
All done! Hit Finish and move on with your day feeling a little more secure.
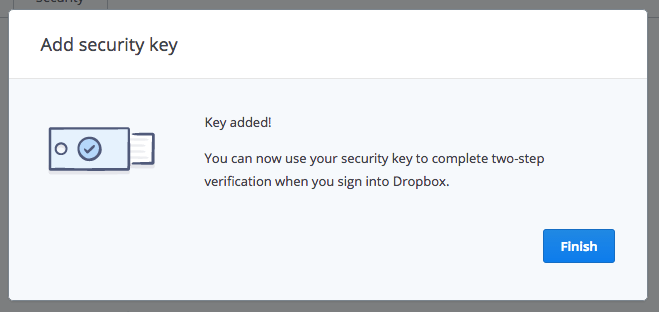
Go to the Add a Security Key page section of My Account. Remove the key if it's already inserted. Click on the Register button. Insert your Security Key into a USB port on your computer.
Completing registration varies slightly depending on the type of security key you have:
Key with a button:After inserting, you should see a blinking light. Lightly tap the blinking circle. You'll see a green checkmark to confirm registration.
Key without a button:This Security Key turns off after each use. Please remove and reinsert the Security Key each time you need to use it. You'll see a green checkmark to confirm registration.
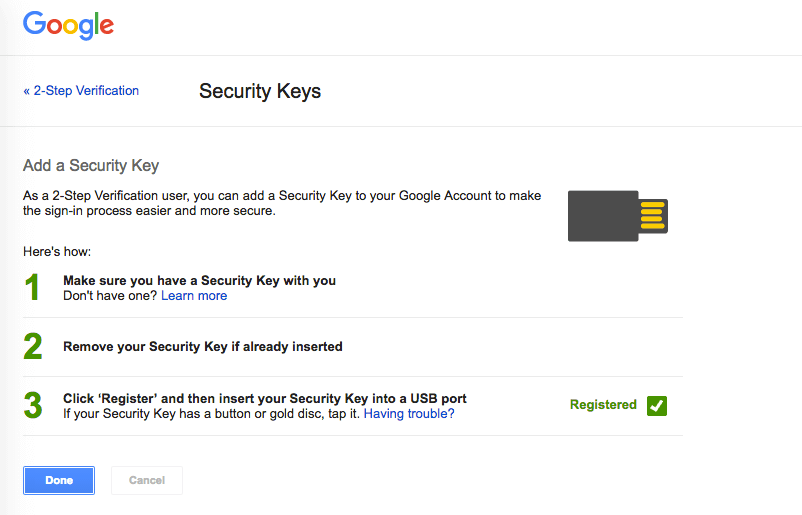
Click Done.
When logging in from a new PC, you'll be prompted to authenticate with the USB security key. Insert the key and press the button when you're asked (if there is a button.)
Some devices and browsers (any browser but Chrome, actually) don't support security keys, so in those cases you can still use SMS verification or another two-step verification method you've configured in your Google account security settings.
Login to Github, click your photo in the top right and go to Settings and then Security. Or just click this link to be taken to the security page. Enable 2FA if it isn't already. Once 2FA is already enabled, click edit.
Next scroll down to the bottom of the page where it says Security Keys and click Register New Device.
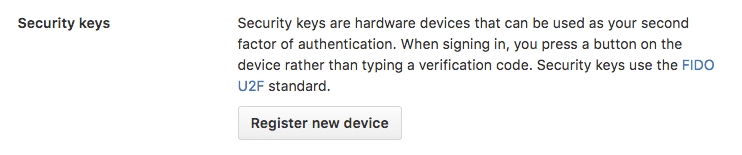
Fill in a nickname, click Add, and insert the key into the USB port and tap its button.
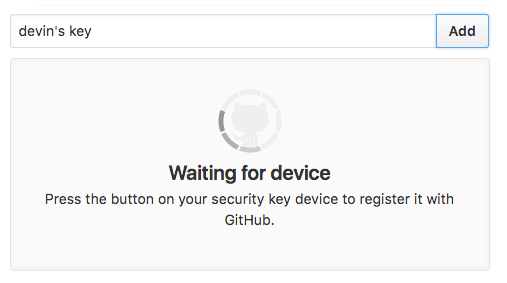
Then you'll have the option of adding another key or deleting existing keys.
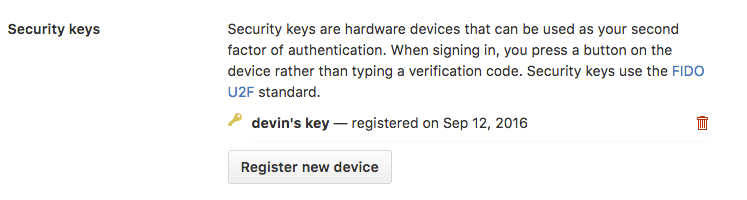
Physical security keys, such as the Yubico FIDO U2F one I'm using, are still somewhat unknown and not yet a universal solution. For example, my key only works in connection with Google Chrome and requires a fully fledged PC (a device with a USB port), but don't underestimate FIDO U2F keys.
The FIDO alliance is composed of several industry heavyweights, from financial institutions to technology and chip makers including the Alibaba Group, ARM, Bank of America, Discover, Google, Intel, ING, Lenovo, MasterCard, Microsoft, NTT DoCoMo, NXP Semiconductors, PayPal, Qualcomm, RSA, Samsung, Synaptics, USAA and Visa.
It might be impossible to use your U2F key on a lot of websites today, but that's bound to change. As the industry moves forward FIDO (or FIDO 2.0 which includes Bluetooth and NFC implementations) along with mobile-style payments (Apple/Android pay using biometric authentication) will be shaping the future of e-commerce and online authentication.
Update:Some of our readers have showed concern if you were to lose your Yubikey. One valid recommendation is to buy two Yubikeys, keeping the second as backup on a safe place. Note however that services that offer two-factor authentication using Yubikey also have recovery mechanisms so that you shouldn't be locked out completely if this were to happen.
 State Senate Honors Vets
State Senate Honors Vets
 Police may track you to an abortion clinic with this tool, report shows
Police may track you to an abortion clinic with this tool, report shows
 Wordle today: The answer and hints for October 24
Wordle today: The answer and hints for October 24
 Apple's Mac week: Are you ready?
Apple's Mac week: Are you ready?
 Go For Broke National Education Center Names New Vice Presidents
Go For Broke National Education Center Names New Vice Presidents
 Making Migrants Disappear
Making Migrants Disappear
 Apple's Mac week: Are you ready?
Apple's Mac week: Are you ready?
 Russia has had 2 leaky space station ships in 2 months. Coincidence?
Russia has had 2 leaky space station ships in 2 months. Coincidence?
 Mas Masuda: A Hero's Century in Orange County
Mas Masuda: A Hero's Century in Orange County
 Rams vs. Vikings 2024 livestream: How to watch NFL for free
Rams vs. Vikings 2024 livestream: How to watch NFL for free
 DMV Director Shiomoto Retiring at End of Year
DMV Director Shiomoto Retiring at End of Year
 Israel’s Permit Regime
Israel’s Permit Regime
 Mystery of interstellar comet 'Oumuamua has been solved, scientists say
Mystery of interstellar comet 'Oumuamua has been solved, scientists say
 iOS 18.2 beta new features: See the full list
iOS 18.2 beta new features: See the full list
 CAPAC Members Condemn Trump Proposal to End Birthright Citizenship
CAPAC Members Condemn Trump Proposal to End Birthright Citizenship
 James Webb telescope just found galaxies that shouldn't exist in deep space
James Webb telescope just found galaxies that shouldn't exist in deep space
 Hubble stuns with new glittering star cluster image
Hubble stuns with new glittering star cluster image
 Anthropic releases AI tool that can take over your cursor
Anthropic releases AI tool that can take over your cursor
 The Significance of Strengthening Ties with Nikkei in America
The Significance of Strengthening Ties with Nikkei in America
 Stuff Your Kindle Day Oct. 24: How to get free books
Stuff Your Kindle Day Oct. 24: How to get free books
Amazon Big Spring Sale highlights: 45 items that are 50% off or moreThe Midterms and the Turn LeftwardFacebook is making it easier to connect with friends againState of the UnionsBest portable projector deal: The Anker Nebula Capsule 3 is $120 offState of the UnionsGoogle's Pixel 9a finally gets a release dateAmazon Big Spring Sale 2025: Best air purifier deals from Dyson, Shark, LG, and moreKitchen-Sink DramaStand on the surface of an alien planet with NASA Wordle today: Here's the answer, hints for January 9 CES 2023: BMW brings another colour All I want from 'M3GAN 2' is M3GAN vs. M3GAN 'M3GAN' ending explainer: How that final shot sets up a sequel 'Quordle' today: See each 'Quordle' answer and hints for January 11 'Quordle' today: See each 'Quordle' answer and hints for January 9 Amazon's 'Hey Disney' voice assistant is coming to your home Echo devices Microsoft may invest $10 billion in ChatGPT maker OpenAI The best moments of the 2023 Golden Globes Twitter's rolling out its own TikTok
0.2094s , 14376.8125 kb
Copyright © 2025 Powered by 【video sex manohara】Enter to watch online.Using a U2F Key to Secure Your Google, Dropbox, and GitHub Accounts,Global Perspective Monitoring